
From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud - Microsoft Security Blog
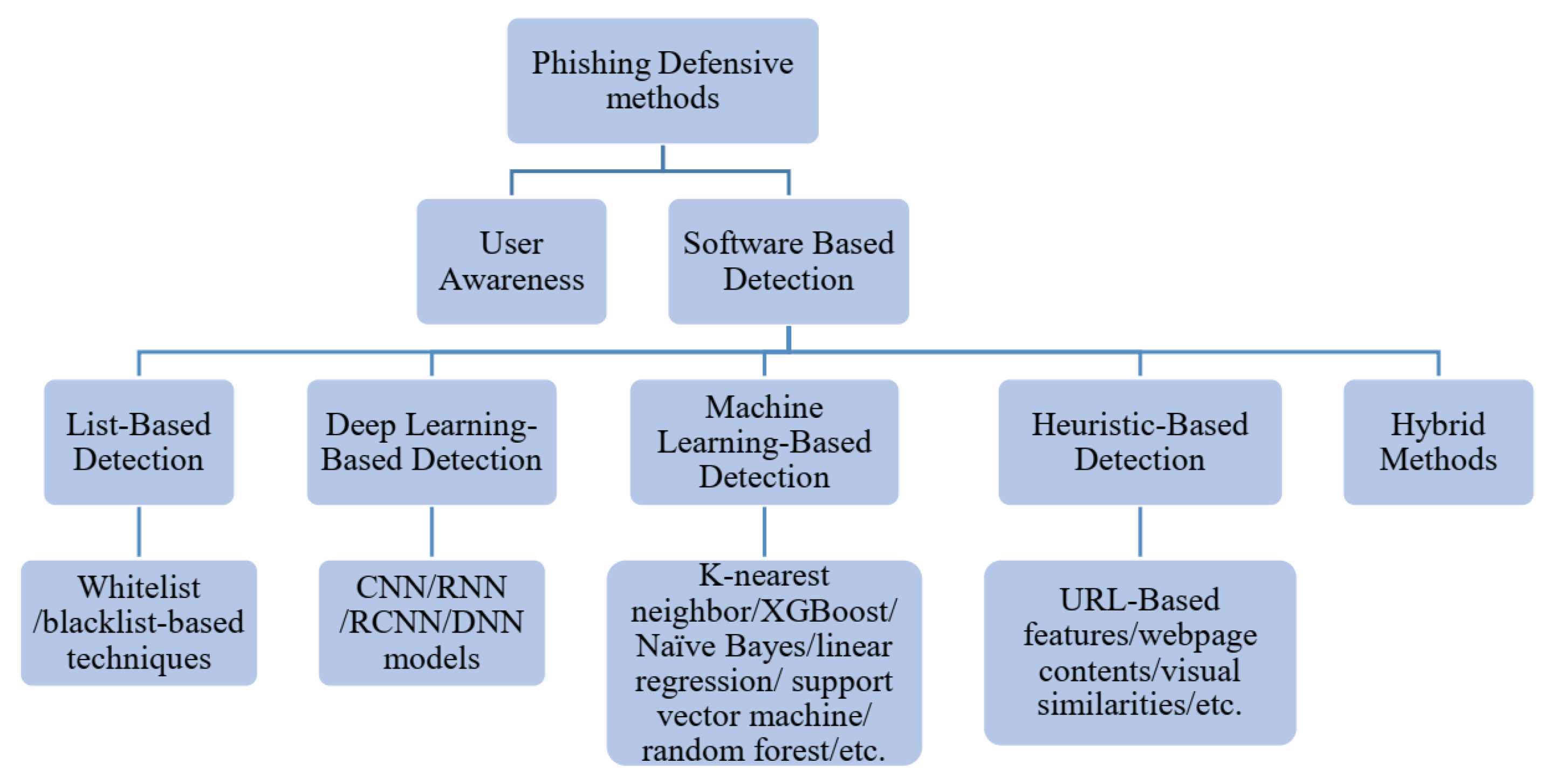
Electronics | Free Full-Text | An Effective Phishing Detection Model Based on Character Level Convolutional Neural Network from URL
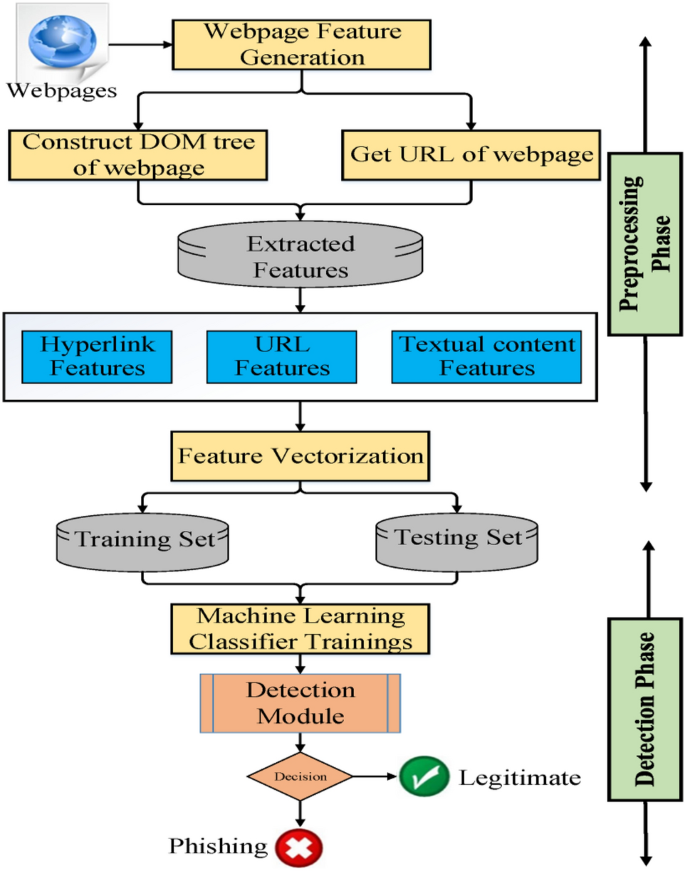
An effective detection approach for phishing websites using URL and HTML features | Scientific Reports
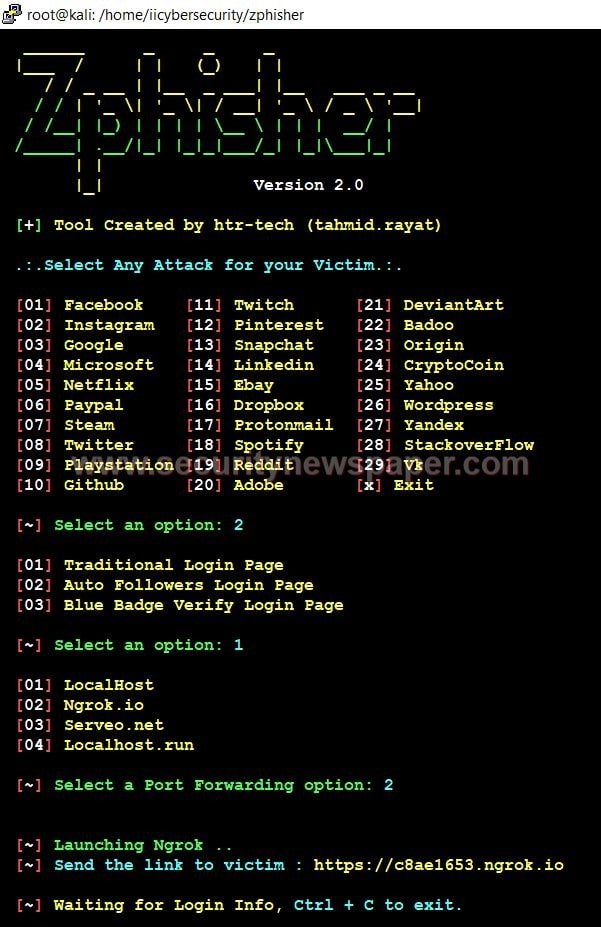
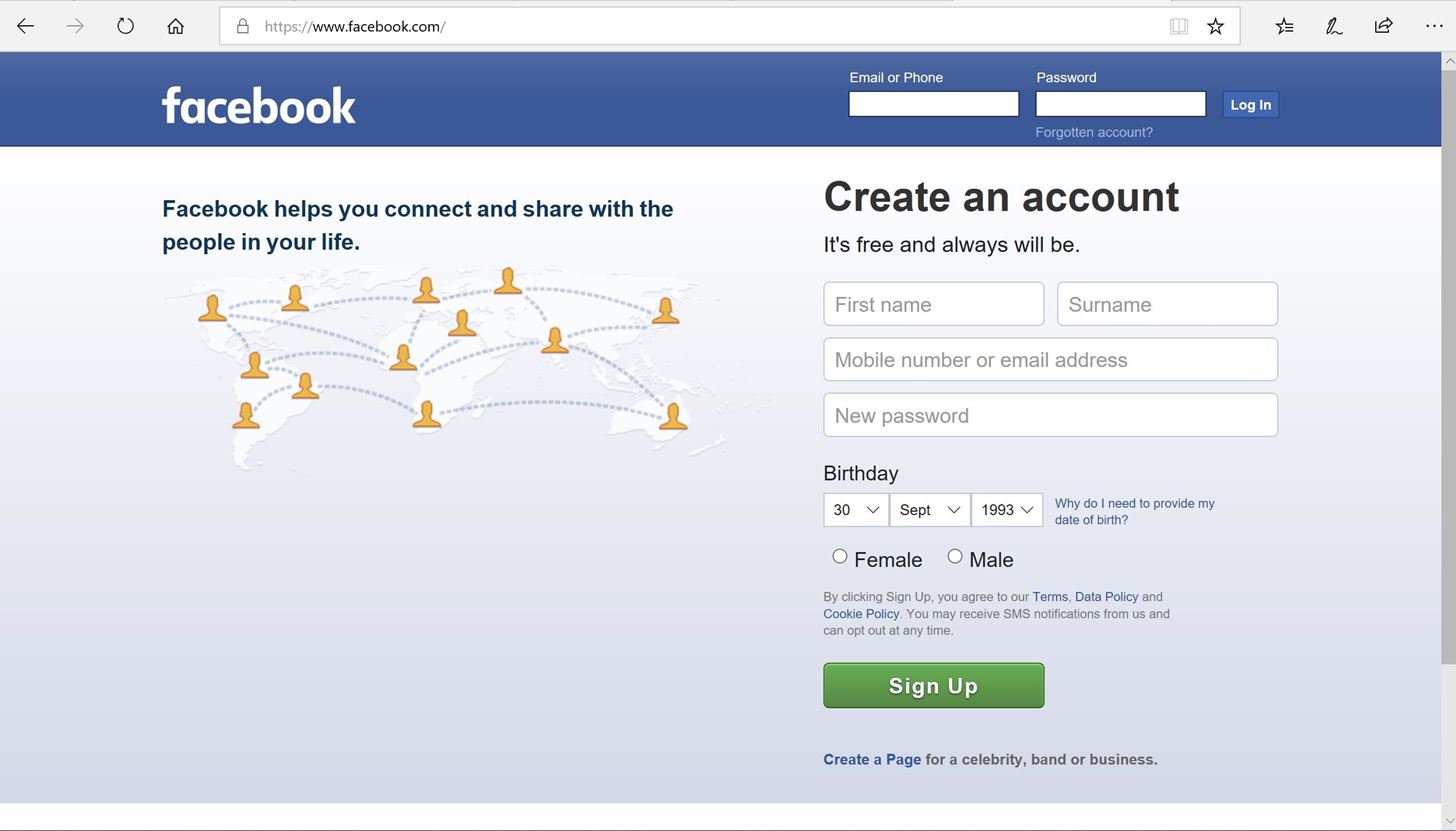

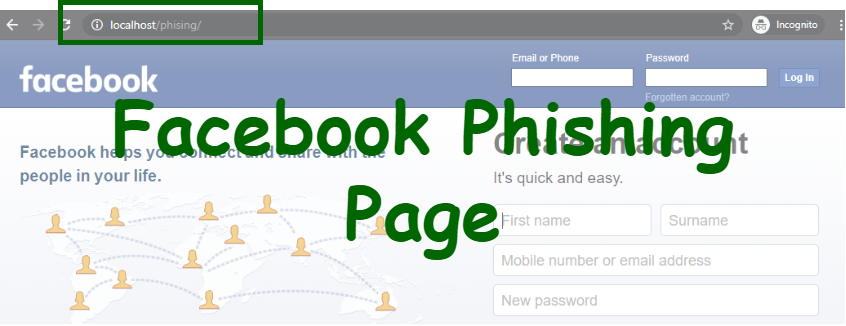
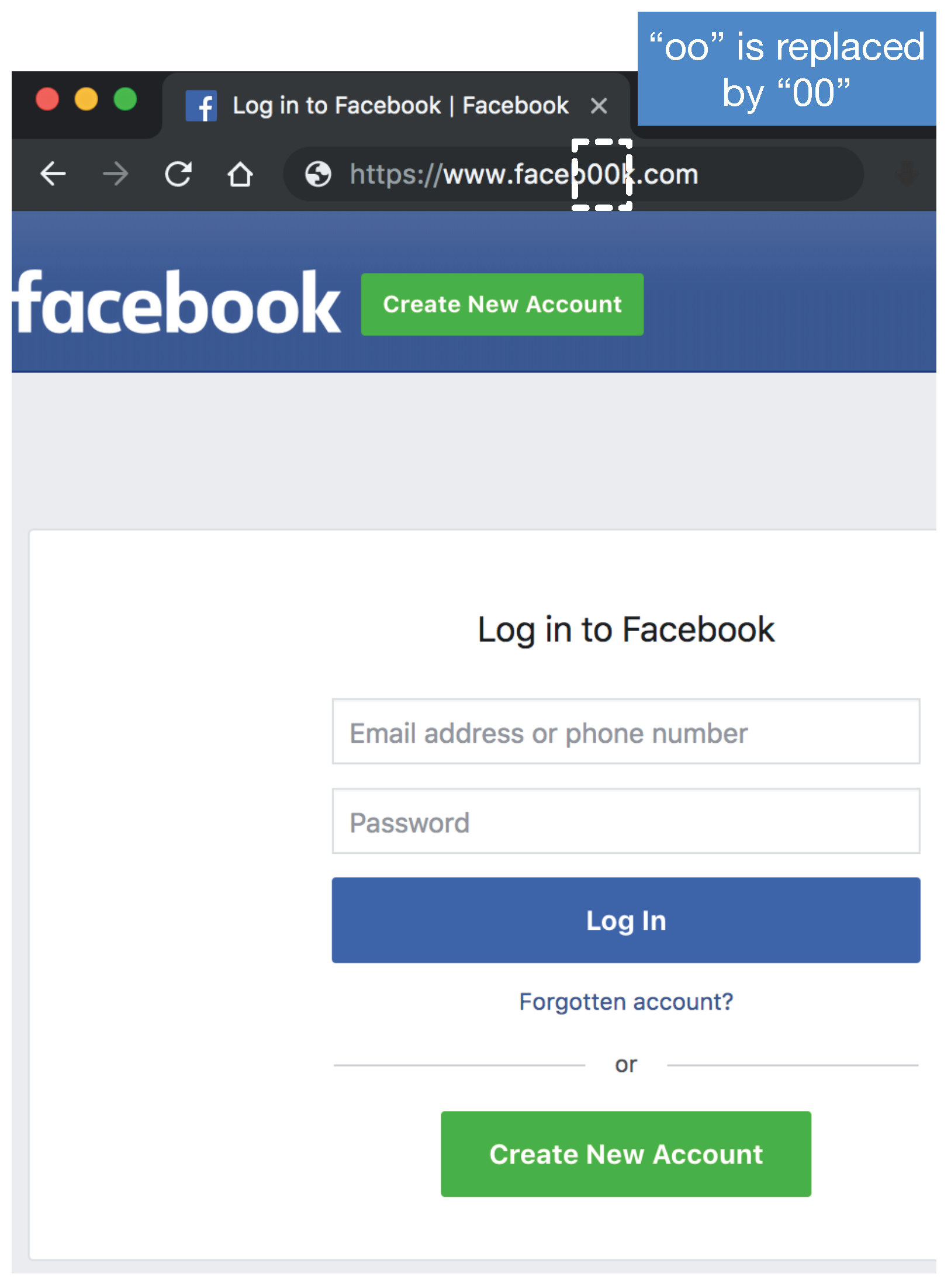


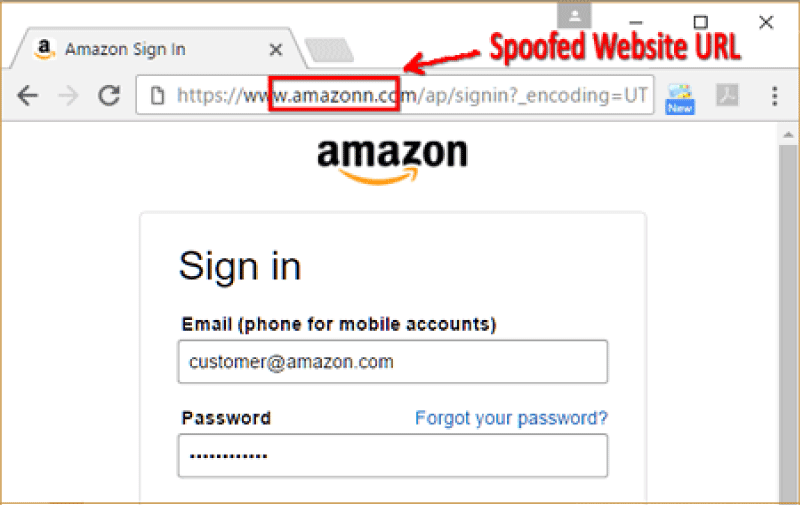

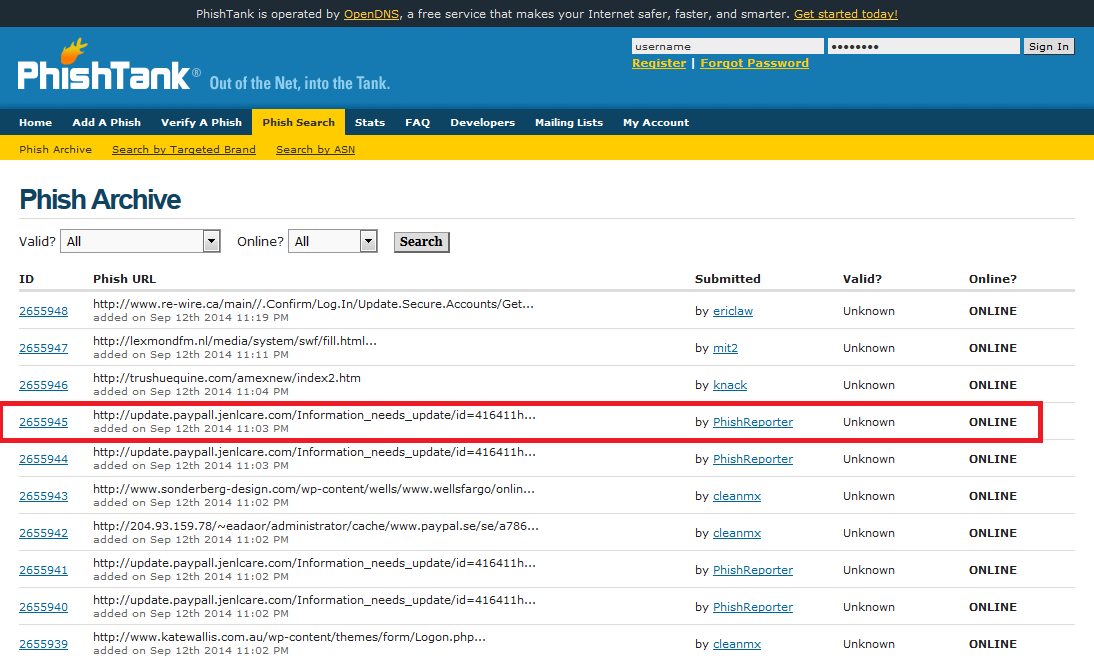
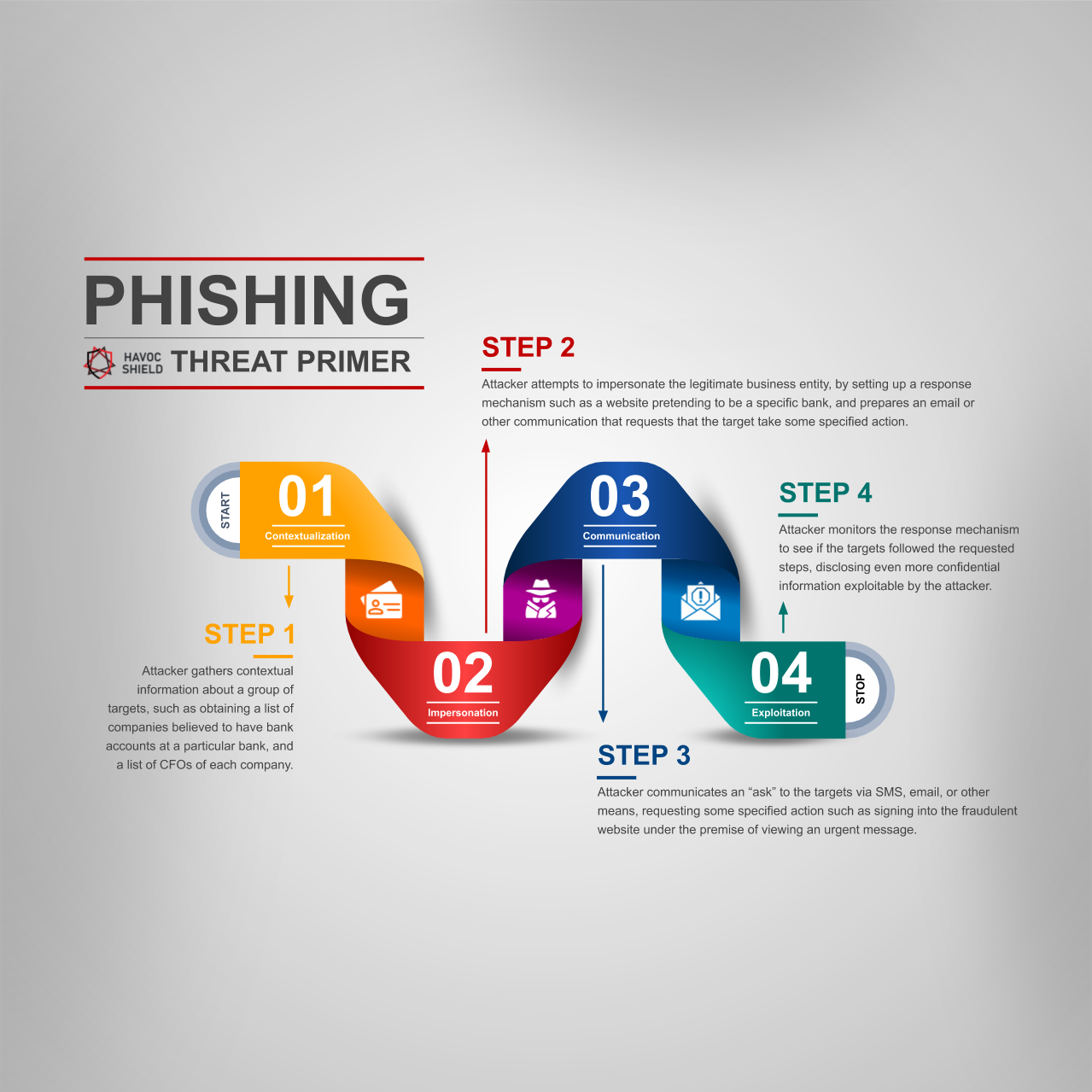
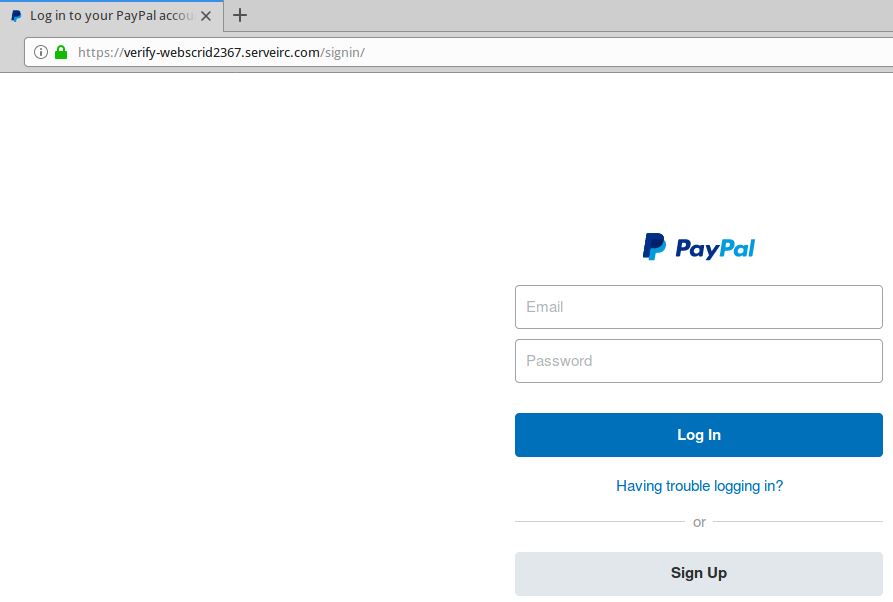
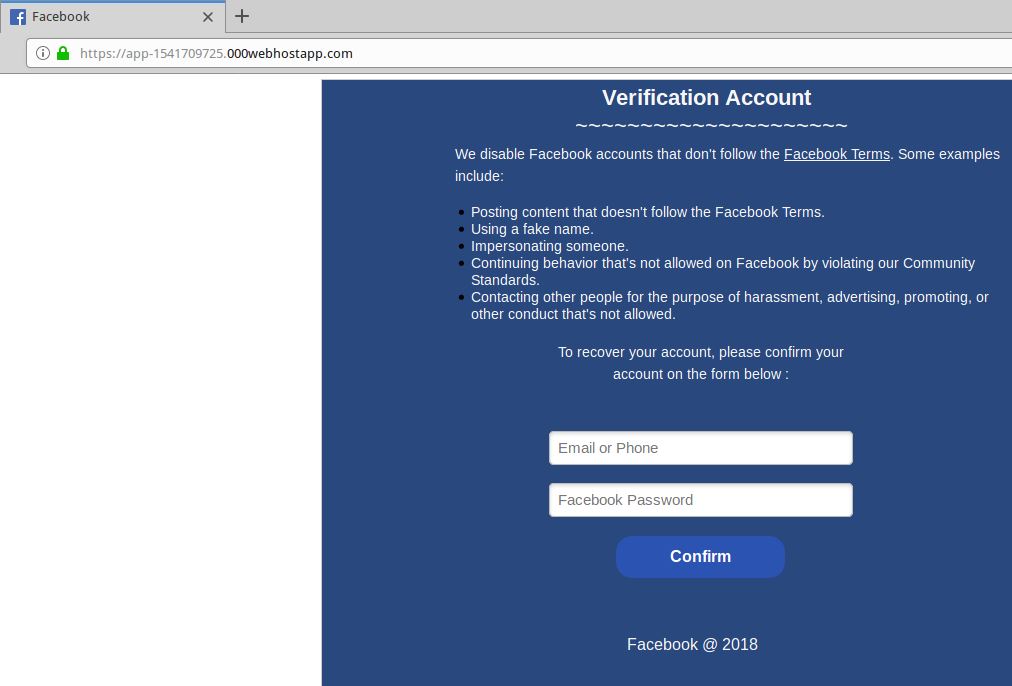


![Top nine phishing simulators [updated 2021] | Infosec Resources Top nine phishing simulators [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/3-13.png)


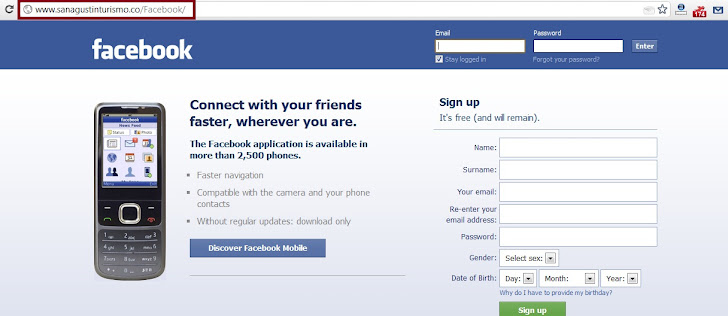


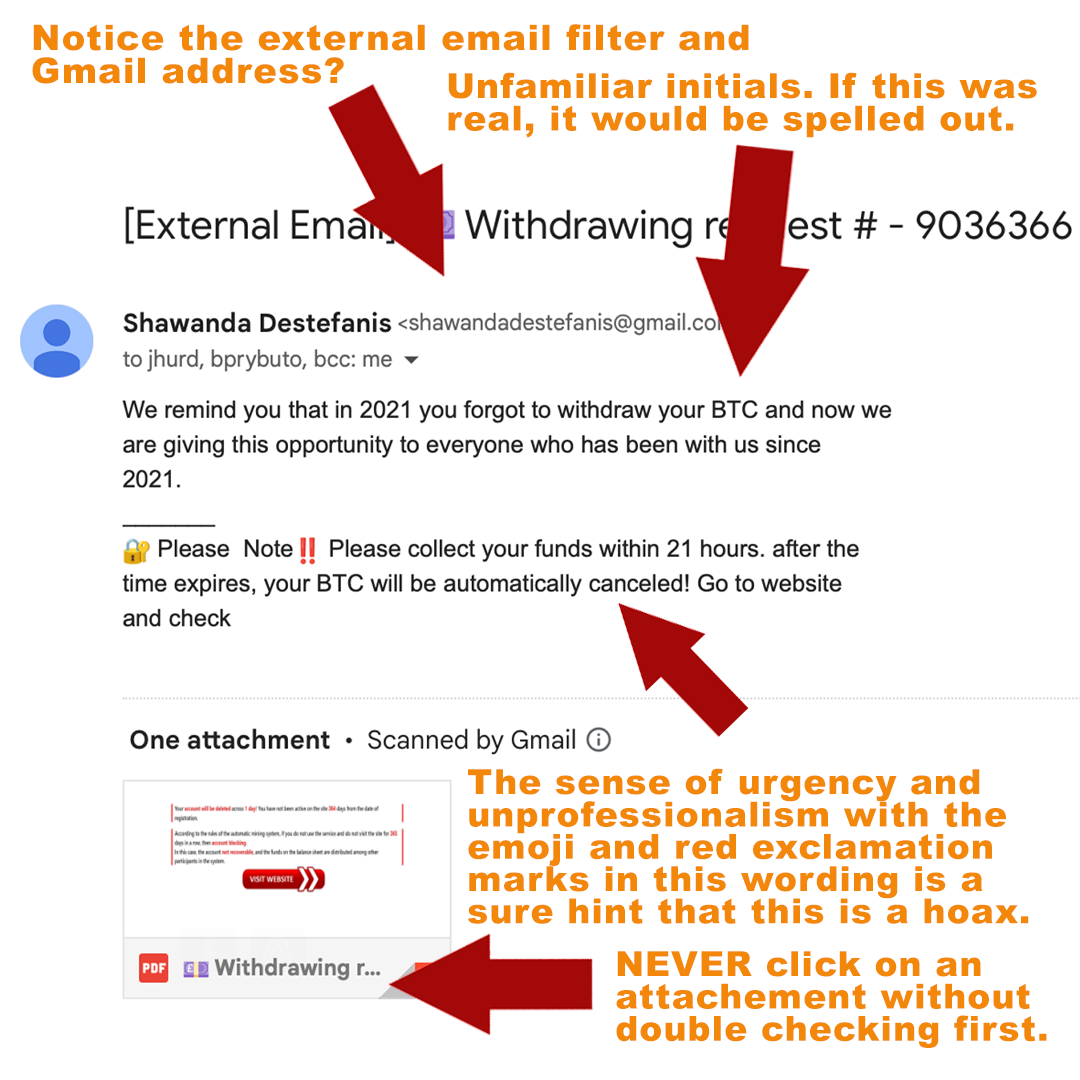
![Top nine phishing simulators [updated 2021] | Infosec Resources Top nine phishing simulators [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2020/08/phishing-risk-test-1140x546.png)