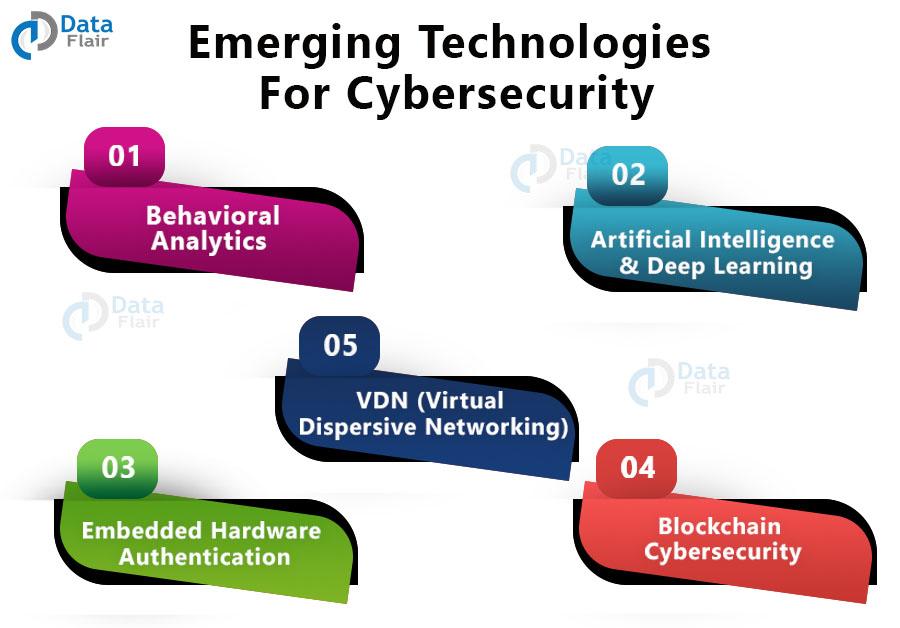
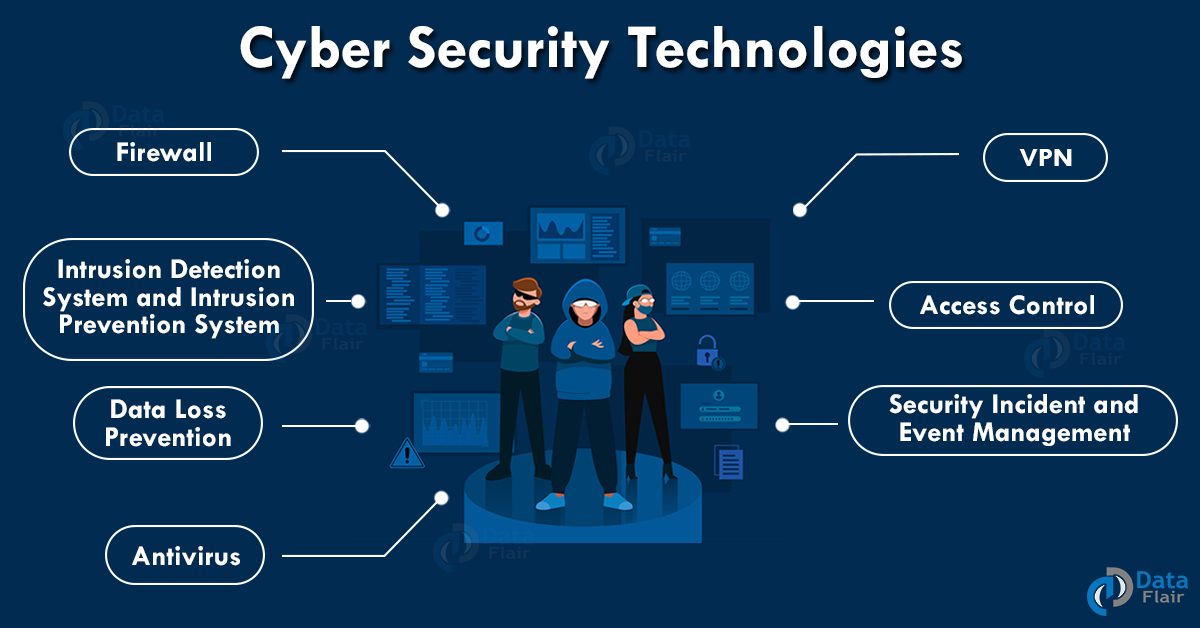
Emerging Technologies in Data Mining and Information Security: Proceedings of Iemis 2020, Volume 3 by Jo�o Manuel R S Tavares
1st day of IEMIS 2020, 2nd International Conference on Emerging Technologies in Data Mining and Information Security - IEM Group

PDF) ************** CALL FOR PAPERS ************** Special Session - Advanced Practices in Cybersecurity and Digital Forensics in IEMIS-2022





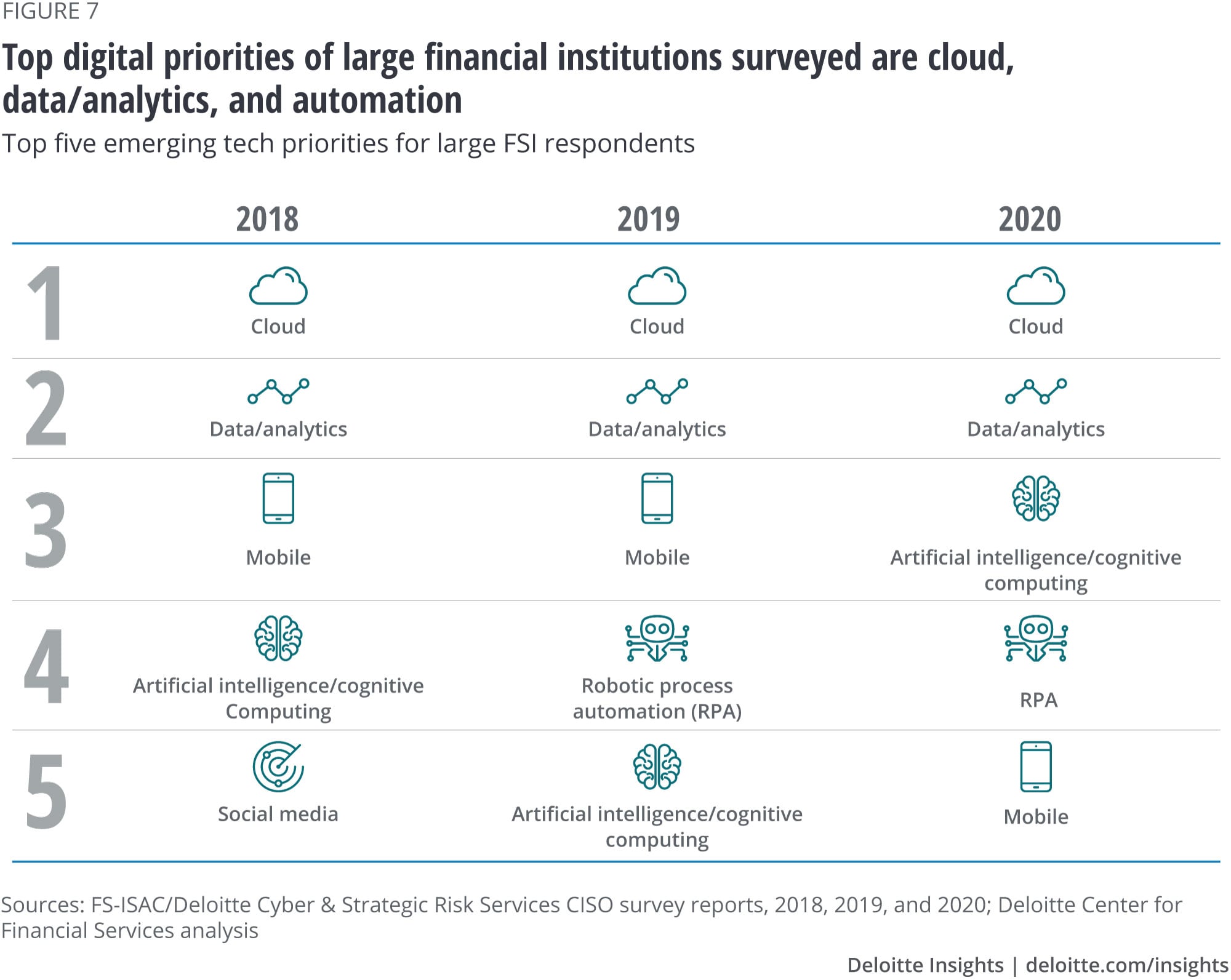
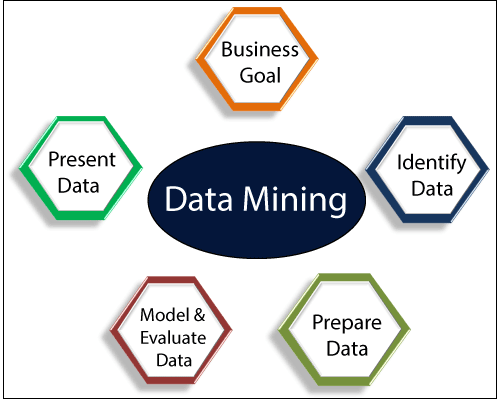




![PDF] Exploiting the Data Mining Methodology for Cyber Security | Semantic Scholar PDF] Exploiting the Data Mining Methodology for Cyber Security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/605c1ec7a2af2b10b81831ab0a49f29a94d47ca7/3-Table1-1.png)