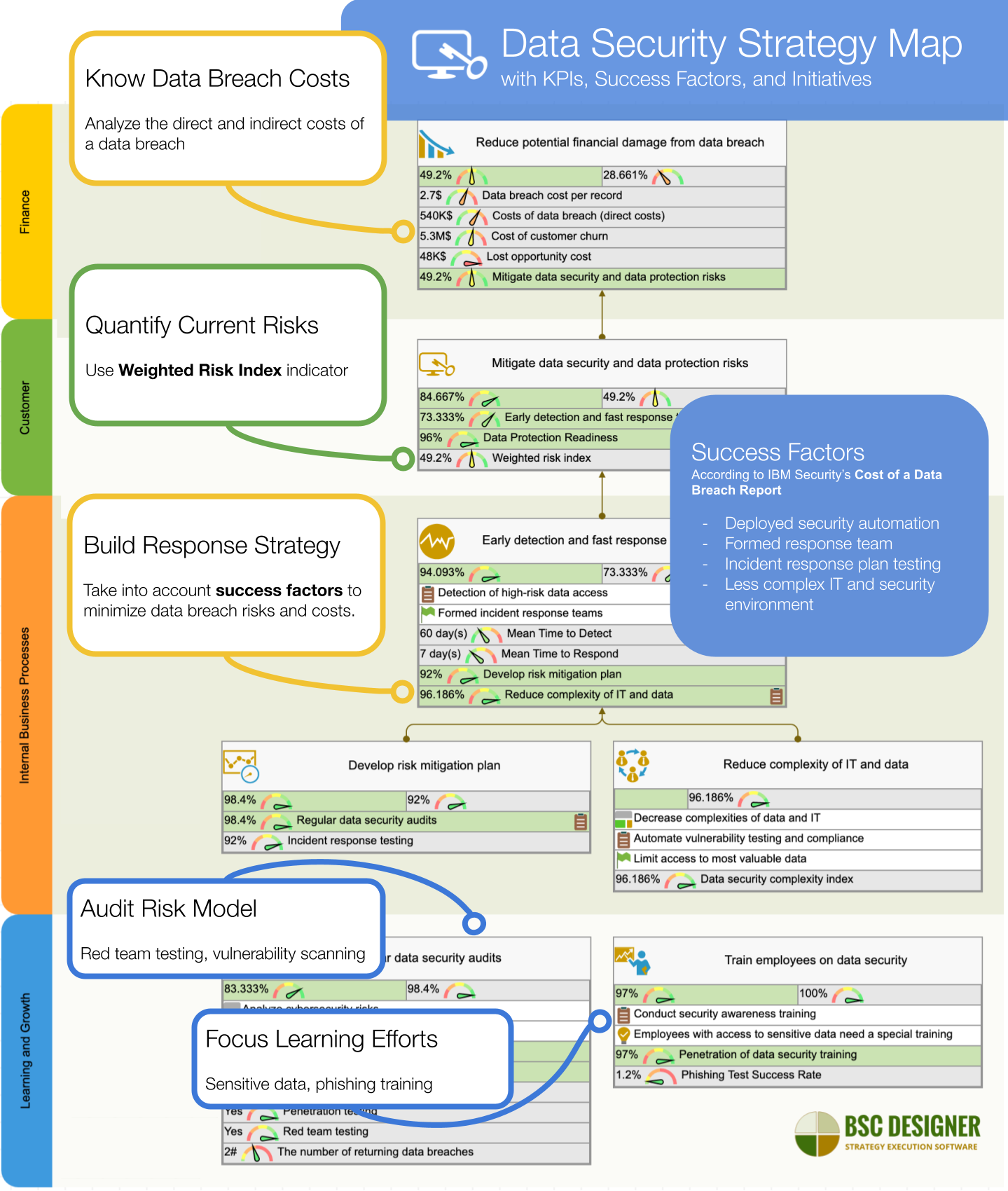
IT Security Metrics: A Practical Framework for Measuring Security and Protecting Data: Hayden, Lance: 0884399587119: Amazon.com: Books

PRAGMATIC Security Metrics: Applying Metametrics to Information Security: Brotby, W. Krag, Hinson, Gary: 9781439881521: Amazon.com: Books

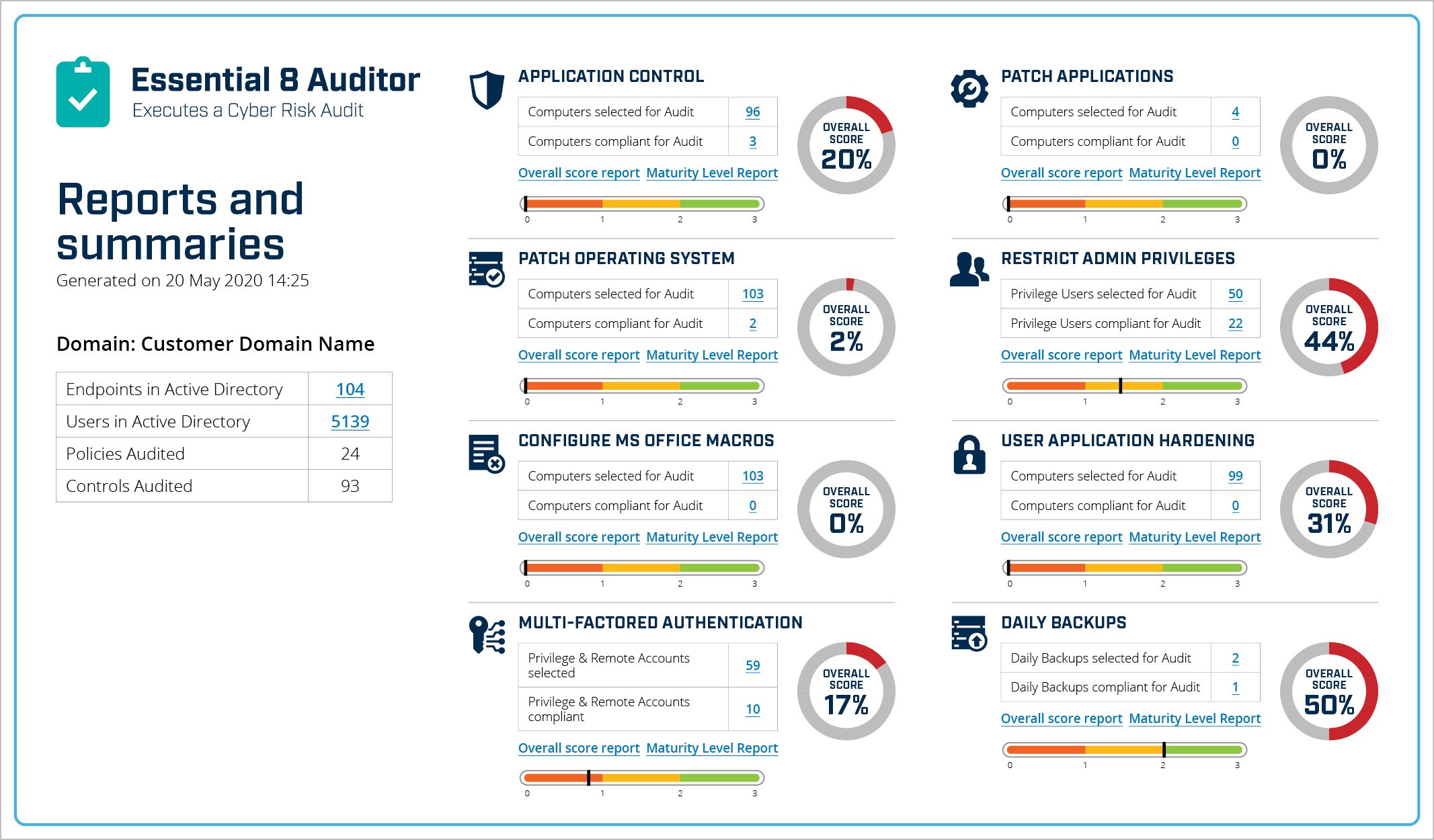

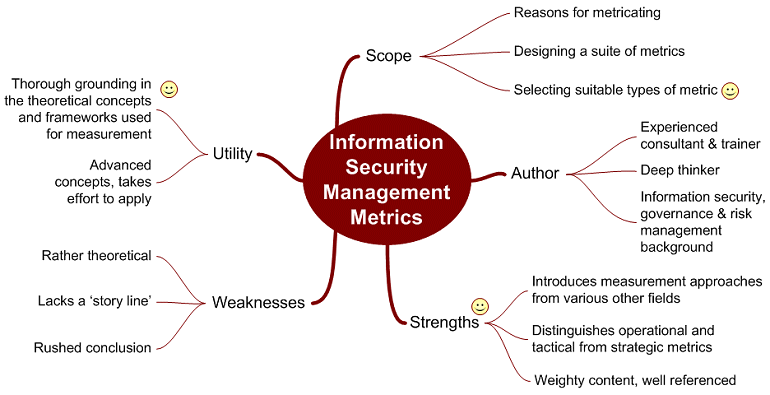
![PDF] Towards Information Security Metrics Framework for Cloud Computing | Semantic Scholar PDF] Towards Information Security Metrics Framework for Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bc587ee2237f259e49965f21cf77265aad49dafe/4-Figure1-1.png)


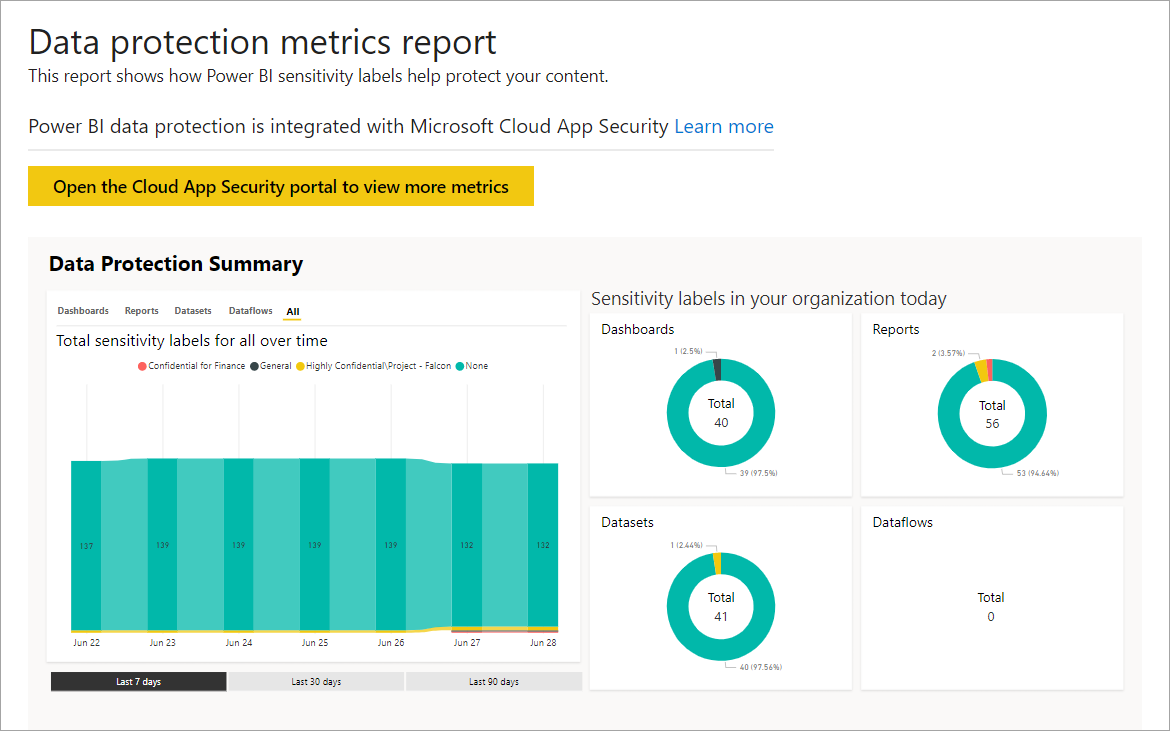
![PDF] Security metrics to improve information security management | Semantic Scholar PDF] Security metrics to improve information security management | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7ccd0015c9b2420e004ebf90697c738a49ebc386/7-Figure2-1.png)