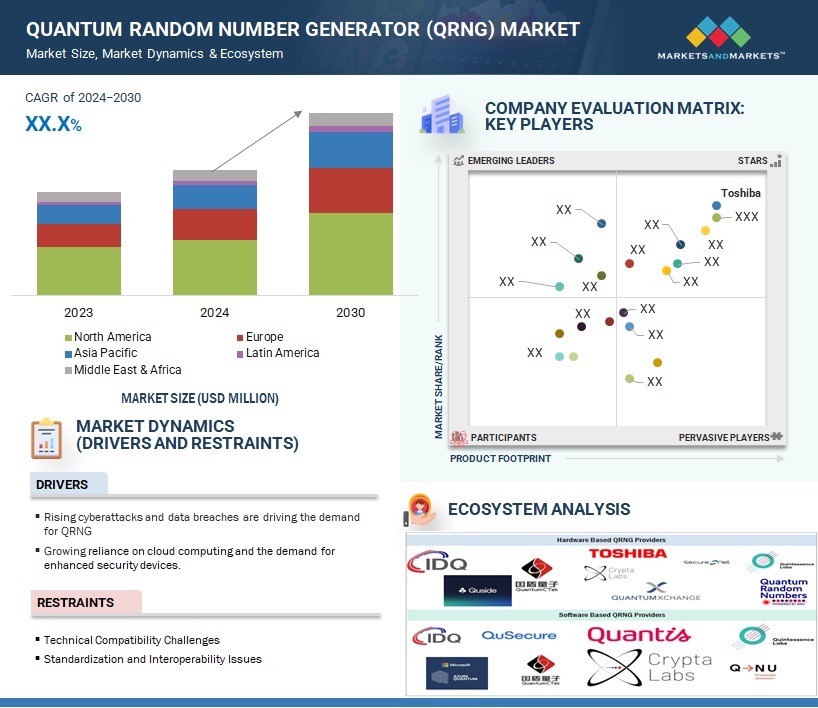
Quantum Random Number Generator Market Size, Share and Global Market Forecast to 2027 | MarketsandMarkets
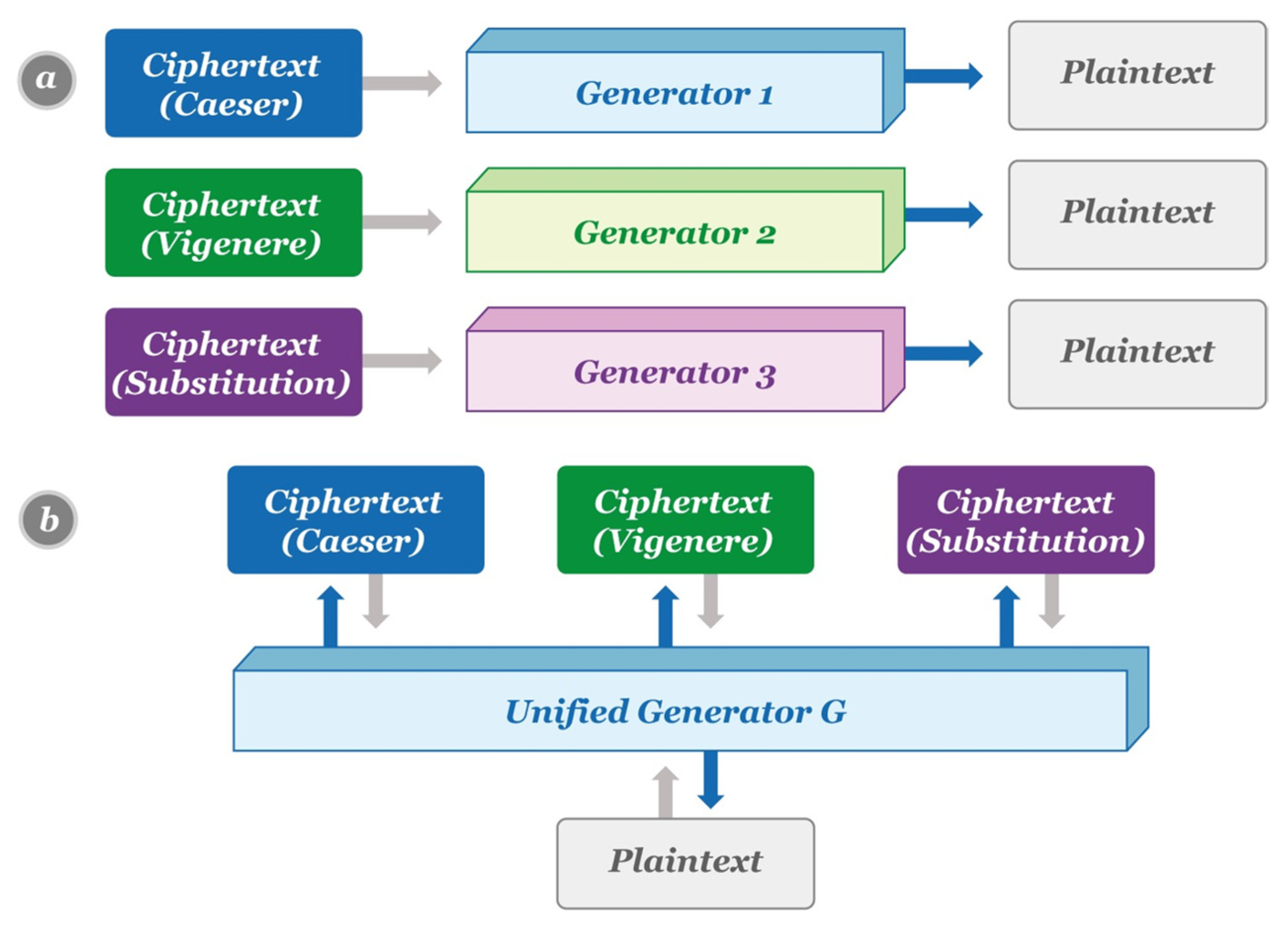
Cryptography | Free Full-Text | Automated Classical Cipher Emulation Attacks via Unified Unsupervised Generative Adversarial Networks

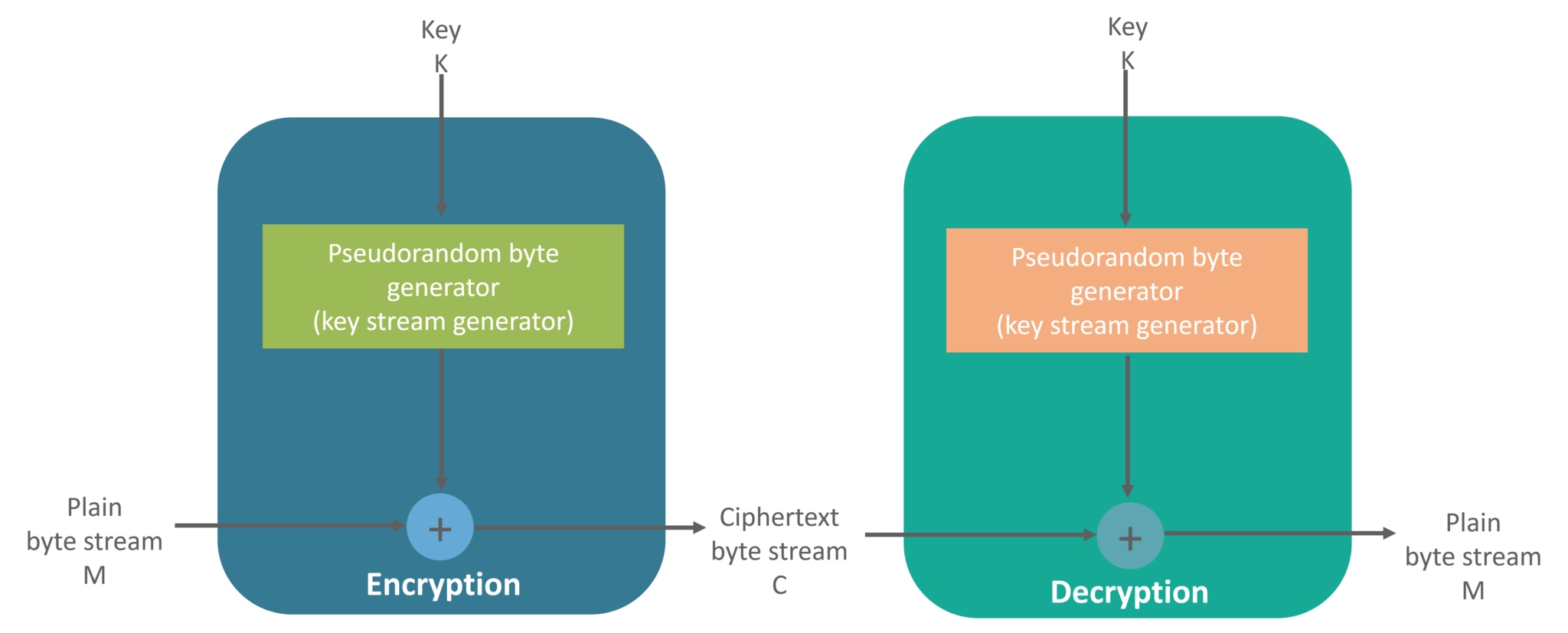
why XOR is recommended/Used in every paper I read for encryption and decryption stream cipher? - Cryptography Stack Exchange
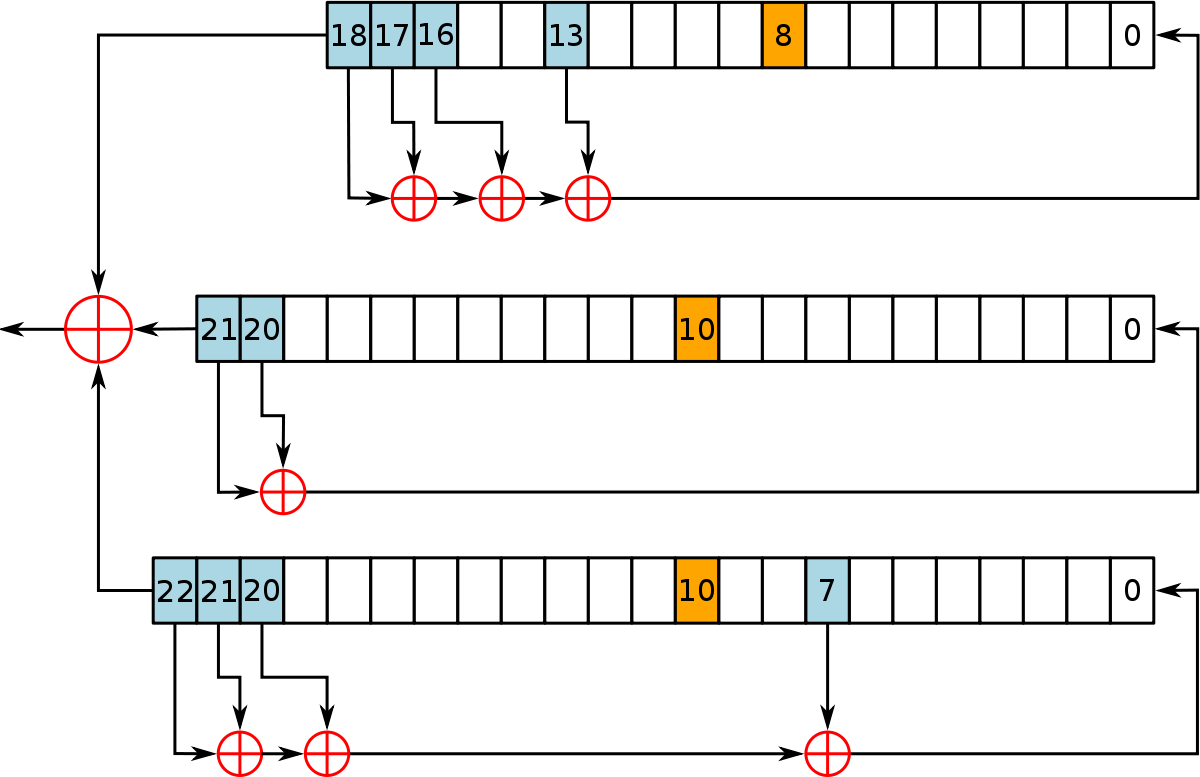
![PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/52d197f4c8881618c40bd36ef98d7cef2c5148f0/2-Figure2-1.png)
PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar
Example of key generation for code-based cryptography. The two matrixes... | Download Scientific Diagram

Distributing a Private Key Generator in Ad hoc Networks: Authority Distribution Using Threshold Cryptography: Stenberg, Eystein Måløy: 9783838387710: Amazon.com: Books

Pseudo-random permutation generators and cryptographic composition | Proceedings of the eighteenth annual ACM symposium on Theory of computing
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology
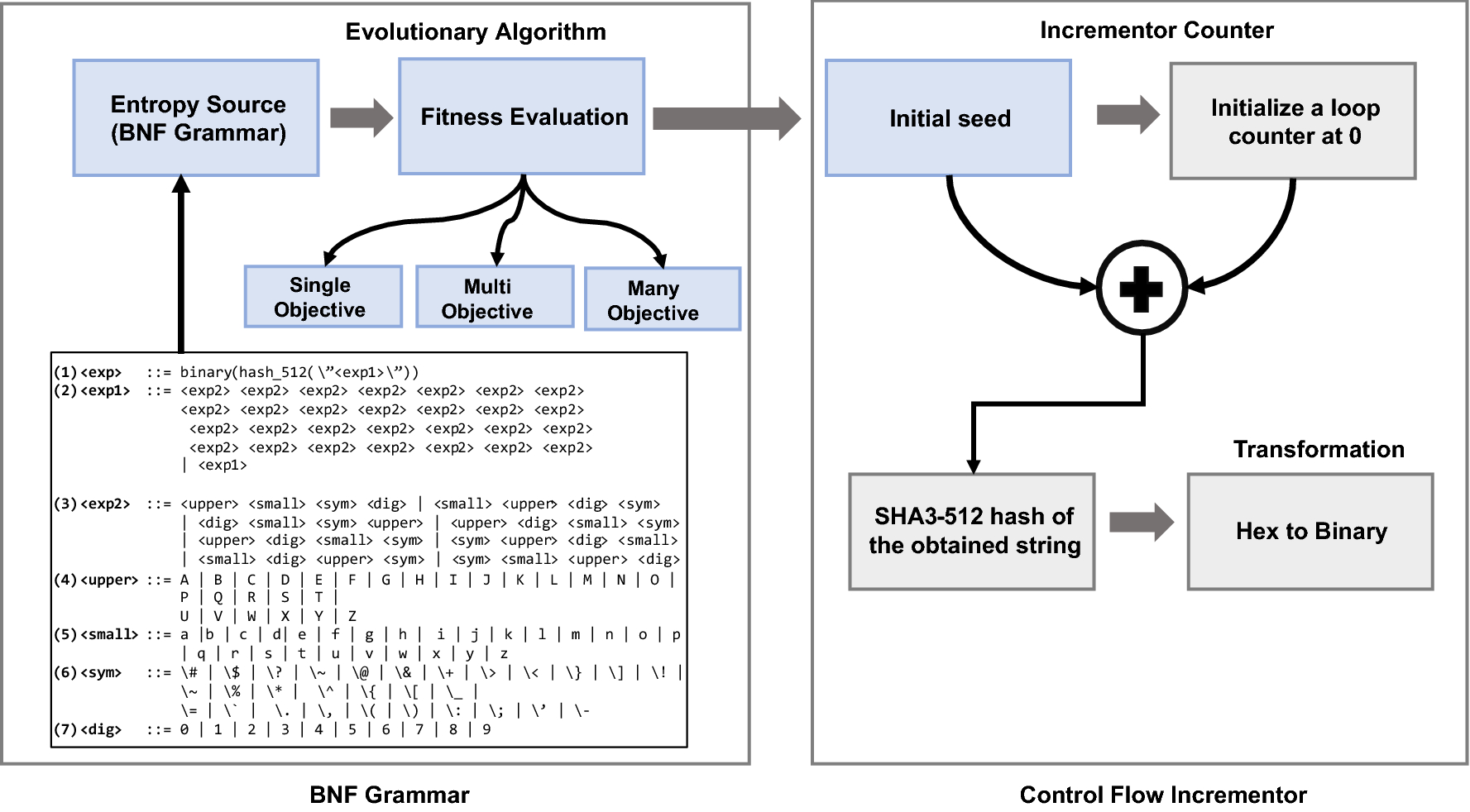

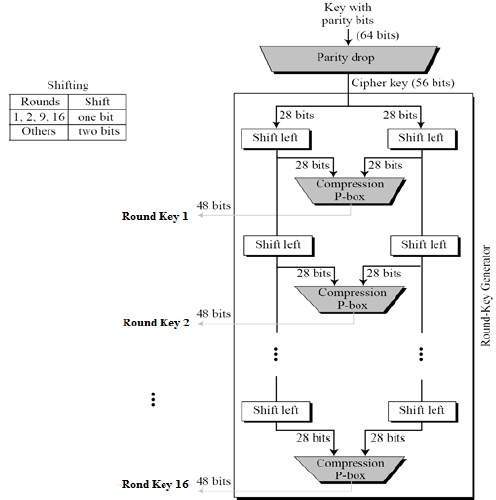

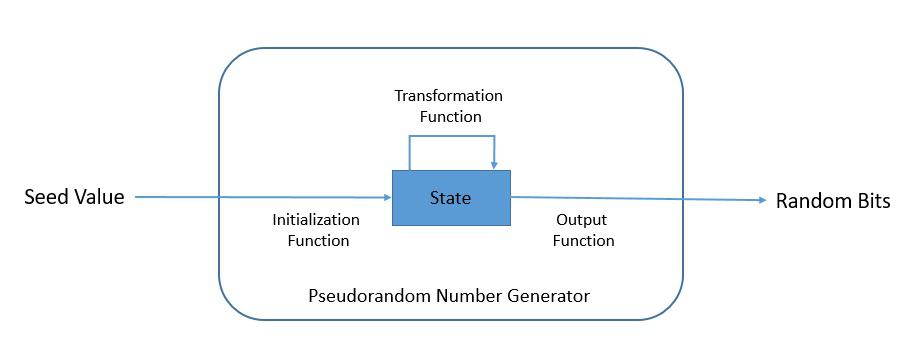
![PDF] Hardware Random number Generator for cryptography | Semantic Scholar PDF] Hardware Random number Generator for cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d40db1ffcac69cd2bab55d7f50159922eaa2b5bf/2-Figure1-1.png)